Quelle: OpenSSH as a secure Web proxy
Transparent Proxy Server
- configure the firewall on your home network to forward an SSH port to the computer you will use as your transparent proxy
- configure your firewall to accept SSH connections on port 2200 and forward them to port 22 on a UNIX-like system on your internal network
- Make sure you secure SSH against common brute-force password cracking attacks on your proxy server.
- Make sure that your server has HTTP access to the Internet through the firewall.
- Dynamic IP address: use Dyndns-client like ez-ipupdate
Encrypted proxy connection
- UNIX-like operating system such as Debian GNU/Linux or FreeBSD
- Example: stable
home IP address of
25.10.101.250 Creating your encrypted proxy connection involves entering a command such as this:
$ ssh -D 8080 -p 2200 username@25.10.101.250- "username” : name of a normal user account on the proxy server at home
- This command creates a local transparent proxy on port 8080 that then forwards all traffic it receives to 25.10.101.250 on port 2200.
- Browser configuration: Manual Proxy Configuration - Socks-Proxy
localhost:8080.If for some reason it doesn’t work with “SOCKS v5,” try switching to “SOCKS v4.”
Quelle: Use PuTTY as a secure proxy on Windows
First, configure a PuTTY session to connect to the UNIX/Linux system you will use as your proxy server. Fill in the following data:
- Host Name (Or IP Address): This may be the domain name for your network, if you have domain name resolution via a dynamic DNS service or other means set up to allow access to your network via a domain name, or it may be the IP address for your router/firewall.
- Port: SSH normally uses port 22, but this may be different, depending on how port forwarding may be set up on your trusted network.
- Protocol: Select the SSH option.
Second, configure an SSH encrypted tunnel through which your HTTP
requests can be forwarded to the system you’re using as a proxy server.
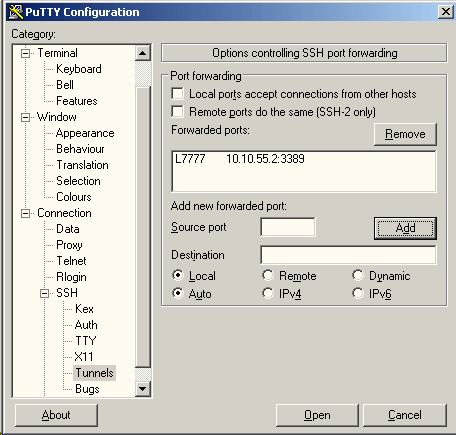
Open the Connection > SSH > Tunnels interface using the hierarchical Categories pane on the left-hand side of the PuTTY dialog box, and fill in this data:
- Source Port: Fill in a port number that will be used locally, on the laptop, for this connection. For instance, you might use port 8080 for forwarded HTTP requests.
- Destination: Leave the text field empty. Select the Dynamic and Auto options.

- Provide Username, save session, establish connection.
Third, configure Firefox to use your encrypted connection. Open the Options dialog box from the Tools menu, then select Advanced. Make sure the Network tab is selected, and click the Settings button. Fill in the following data:
- Configure proxies to access the Internet: Select Manual Proxy Configuration.
- SOCKS Host: Enter 127.0.0.1 into the text field.
- Port: For the SOCKS Host, fill in the same port number you specified in the PuTTY tunneling dialog — 8080 in the above example.